Introduction
First time I worked on a computer was in high school; just 2 years before finishing my school. Floppy disks (not discsJ) were more common those days and I never heard of thumb drives. I remember the day I find an option to hide a folder; it was late night and as usual I was doing something on my PIII, I was able to hide a folder but struggled for more than couple of days to get it back. I was excited; I got something to hide my data. Than after 6 months or so MS launched WinXP; I installed it after a month. I got very excited when I saw that one user cannot access data in another user’s folder. The ‘Access Denied’ message gave a happy feeling. Though I never really needed any type of data protection that time I was happy that if needed I can do that. Than with time I learned lots of other measures and with time I used to update measures I use to protect my data.
Let’s see what I am doing now a day to protect my data. Four five months back all of my data which needed protection was encrypted with three layers of world class encryption algorithms; first layer encrypts data using AES algorithm, second layer encrypts data using Twofish algorithm and third layer encrypts data with Serpent algorithm. So that’s something which even all combined computing power of this world will not be able to break in life time of our universe. But now a day my data is encrypted with only a single algorithm; AES. I used three layers only to experiment and even this single layer of protection is more than enough that US Defence department is using this algorithm for there classified docs, so I think for me this is enough. And my system got very slow due to real time encryption/decryption of data passing through three layers of heavy encryption so I am no longer using that implementation but yes it feels really cool to know that yes the baby is protected.
People think that if they have a password protected account then no one can access there data. Guys this is not true, I can any day put a Linux Live disc and can copy anything I want. Now say you have a laptop and used to travel a lot, in this case Windows protection is not sufficient. You need encryption to protect your data as for most users there data is more valuable than the laptop. So in this post I am covering security measure you can keep for such a scenario.
There are hundreds of solutions to do what I have just explained; some are good, some are pretty complex, some are free, some are paid, etc etc etc. I am using TruCrypt which is free and open source software. Guys believe me this is really good software which gives you very good options to secure your data which even top class paid softwares cannot match. I am using this software from more than 2 years and it still have to crash; I still have to see any other software which is this much stable. This software is really rich in options; today I am covering just the basics so that you can start using the software. I am only explaining how to encrypt a partition with a user defined string, in future posts I ll cover more features and capabilities of this software like hiding data inside an already encrypted partition, using keys files to encrypt data, encrypting whole system, etc.
Installation
I am just mentioning the main steps here:
Step 1
Here you have two options; one is Install and other is Extract. Use Extract only if you need to use TrueCrypt on multiple systems without installing it; like want to carry it in a Thumb drive. Only thing you cannot do with Extract option is encryption of system drive otherwise more or less things are same. Keep defaults for all other options
Step 2
So that’s all in installation.
Steps to Encrypt Data
Now let’s see how all this works.
Step 1
This is interface; straight but yes little complex. Let’s start with encryption; click on Create Volume button.
Step 2
You will get three options. As I am only covering encryption of a (non system) partition in this post, select second option.
Step3
Keep first option selected. Second option is very complex and is needed when due to some reasons you have to reveal encryption keys/password; yes you can even keep your data protected in case someone get access to your keys. I ll cover this thing in future posts, for now keep first option selected. Yes do read the long message written below the second option; it’s interesting.
Step 4
Click Next and then click on Select Device; you ll get a similar screen as shown above. Here you have to select the partition you want to encrypt. I have two hard drives; one of 8GB capacity and another of 2GB capacity having one partition each, here I am encrypting second partition. Guys always name computer partitions, like here I have named the partition to Data. I have seen many people formatting wrong partition; name given to a partition goes long way to keep these mistakes in check. And yes don’t ask me from where in this world I got 2GB hard drive :)
After selecting the partition you will get a long warning. If you want you can read it, in end you have to click on Yes.
Step 5
Now you can select whether you want to format the drive before encrypting. If you already have data in the drive then you can choose the second option otherwise choose the first one. Say you have 200GB partition and have couple of GBs of data in it then its better to copy that data to another partition and choose the first option. Formatting will make the process very fast otherwise be ready to sit for couple of hours just to encrypt a 200GB partition. I am choosing the first option as the partition I want to encrypt is blank.
Step 6
Now you get the main options related to Encryption algorithms and Hash algorithms. Just for curiosity let’s choose three layers encryption I just talked about, but as said only AES is much more than needed. There is a Test button; you can click on this to check performance of various algorithms. Keep Hash algorithm as default, I ll keep the explanation on this for some other day. Do remember that there is a large performance impact especially if you choose multiple layers of encryption.
Step 7
Enter the password; min 10 characters long. I ll explain concept and usage of Key files in a future post.
Step 8
In FileSystem drop down choose NTFS; FAT is useful only for partitions (or file containers) less than a GB in size. Do read the ‘Important’ note in the window. Most people don’t know that when you delete a file it still remains there and can be easily recovered. So if you want that no one can recover such past deleted data keep Quick Format option unchecked, in case you don’t want to wait for ages to get this thing completed and there is no critical data which you have deleted in past than check the Quick Format option. Then click on Format button.
Step 9
You ll see a progress bar. See for a 2GB partition my system will take more than 10mins, so if you have 200GB partition better to check Quick Format option otherwise all this might take more than 10hours. Performance would increase by 2x or more if a single algorithm is used.
Step 10
So that’s all about encrypting the partition. Now you cannot use the partition directly, you have to first Mount the partition using the password you just entered. But first see what happens if you try to access the partition without entering the password and this is something you should understand.
Step 11
See after encryption as Windows is not able to access the drive, it refuses to identify the partition. Look carefully that you can still format the partition, yes one can format the partition and use it but the person cannot access your data. So this method only prevent unauthorized access and do not protects the data, feel free to ask your question in comments section if you have any doubt on this. So if you think such things can happen do have backups of your data; you can encrypt your data and burn it to optional discs so that no one can access it but yes someone can still break the discs.
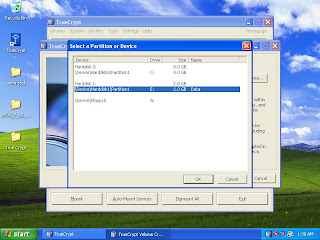
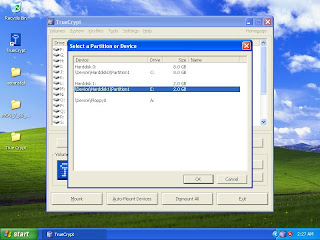
Now to access you data you have to first ‘Mount’ the partition from the software. Run the software and click on Select Device button.
Step 12
Select the partition and click on Ok. Internally this software will mount encrypted E drive to another drive letter. As you cannot use E drive letter to access the data, you have to choose the drive letter on which you want to mount the encrypted partition. I am selecting R here; then click on ‘Mount’
Step 13
System will prompt you for password. Enter the password and click on Mount, then open My Computer.
Step 14
Now you have a new partition with drive letter R. You can use it as any other partition.
So Guys that’s all about encrypting a partition. In future posts I ll cover more capabilities of this software and this approach.
Points to remember/best practices:
- This approach only prevents unauthorized access to your data under any attack but anyone can still delete all of your data.
- No need to encrypt things like multimedia things, games, etc.
- Best is to create a separate partition for data which needs protection and then encrypt it.
- This method will not protect your data from world’s top security experts. AES or any other type of encryption is still venerable to Side Channel attacks but I doubt you need that much protection.
- There is no way to get your data back in case you forget the password.
- Windows reinstallation will not affect your data/encryption and you can still access your data. In case of Windows inbuilt encryption (available with Professional, Enterprise and Ultimate Editions) if Windows got corrupted or something similar happens you also loose access to your data.
- You can access your data anywhere; you only need the software and the password.
- AES is the weakest algorithm in all these but is much more than enough. Why I am using AES is that it’s compatible with almost every other encryption system and software.
- There is big performance impact if you want to do heavy read/write to the encrypted partition. For data like documents, movies etc this is not a problem.
- If you have large amount of data and you don’t want any performance impact then go with Intel Corei7 processors; couple of Corei5 processors can also do the job. These processors have hardwired support for AES. I ll cover the technical details in a future post.














Thats very helpful info. Till date i am using the winzip passwords but this seems much better way.
ReplyDeleteWaiting for your post on more capabilities on this software; please post soon
I think it is 2 GB in your post
ReplyDeleteFormatting will make the process very fast otherwise be ready to sit for couple of hours just to encrypt a 200GB partition
@Anonymous
For winzip, i need to zip and unzip again and again.
@MANN
Can something like this be done, if someone tries to open my paritition, it asks for a password, if correct password is supplied then only it gives access.
And second thing, please enable e-mail subscription on your blog, I would like to subscribe.
get it from www.feedburner.com
Do visit my blog : http://javakafunda.blogspot.com
This comment has been removed by the author.
ReplyDeletewassup sir ji.. no new post
ReplyDelete